6
The Disoptimized
The Ambiguous Tactics of The Pirate Bay
ON JANUARY 31, 2008, Swedish authorities filed charges against the three administrators of the infamous site “The Pirate Bay” (TPB): Fredrik Neij, Gottfrid Svartholm Warg, and Peter Sunde. The trial of the site’s administrators was one front in a long battle to remove TPB from the internet. The website had served as the homepage for internet piracy since its launch in 2003 and belonged to a broader propiracy, anticopyright movement in Sweden.[1] This informal movement included political parties and think tanks, while the TPB team coordinated an easy-to-find and politically vocal website that facilitated mass piracy. The website acted mostly as a search engine for BitTorrent files, allowing people to search for legal and illegal content shared online and had also acted as a tracker that coordinated this Peer-to-Peer (P2P) file sharing for a time. As it was one of the most popular websites in the world, TPB’s web traffic gave its administrators political influence that they leveraged to become critics of copyright and proponents of free copying. Jonas Andersson Schwarz, who has written an in-depth history of the group and its relationship to online file sharing, describes their politics as “a publicly visible stance, supportive of unrestricted file-sharing.”[2]
The events that led to the TPB trial and eventually jail time for its administrators began two years earlier. Police forces raided TPB, confiscated its fifteen servers, and arrested three people on May 31, 2006.[3] Reports later indicated that international groups, specifically the Motion Picture Association of America (MPAA), pressured the Swedish government and police into action.[4] After the raid, the MPAA released a statement celebrating the end of the site. The Pirate Bay countered by bringing the site back online three days later with their usual logo replaced by a phoenix rising to celebrate its resurrection.
TPB’s political and practical support of copyright infringement made them a key target of Hollywood’s war on online piracy. Hollywood, to be fair, was just one copyright holder antagonized by The Pirate Bay’s admins. With sly, offensive, and rude remarks, the “Legal Threats” page on their website cataloged their responses to the frequent requests by media firms and rights holders to remove infringing torrents. In their various replies, administrators explained that they kept the site as open as possible; TPB did not censor any of the torrents on their server. As spokesperson for TPB, Sunde explained in an interview: “We have created an empty site where the only condition was that you cannot upload something where content doesn’t match the description or if it blatantly is criminal in Sweden.”[5] Elsewhere he says, “we have a strong policy at TPB that we do not censor anything.”[6] As court cases shuttered other P2P networks, TPB endured as a global symbol of online piracy. Nonetheless, keeping the site online had not been easy. It had faced numerous challenges, including constant legal threats, police raids, and domain seizures, and now the administrators faced jail time.
Ultimately, the trial was as much about securing infrastructure as it was about copyright. The pirates popularized BitTorrent and pushed to make BitTorrent networks more difficult to manage. These tactics undermined the work of daemons, especially the use of Deep-Packet-Inspection (DPI) technologies to protect copyright. While there has been much discussion of the legal maneuvers of the group and its trial,[7] there has been less focus on the group’s infrastructural tactics. Behind the symbol of a phoenix rising that appeared on the relaunched website was a lot of technical work. Following police questioning, TPB’s admins and volunteers had quickly rebuilt the servers and other infrastructure needed to keep the site online. The relaunch ended up being one of the many ways that the advocacy of TPB turned to matters of internet infrastructure, and ultimately to the work of daemons.
Where hexes and wards repel demons, P2P and “dark” networks (“darknets,” anonymous networks) repel internet daemons. In their struggles to stay online, TPB admins tried to discover the limitations of daemonic control and then undermine it. This conflict happened deep within the internet’s infrastructure, largely outside public view. TPB relied on new developments in the BitTorrent protocol to become more difficult to shut down. Eventually, they tried to shield against the watchful gazes of daemons by launching a virtual private network (VPN) that encrypted its customers’ packets. These tactics help not only to define the limits of flow control but also to introduce an alternative to polychronous optimization. For all the antics on the TPB website, its admins and its broader movement are primarily motivated by a desire for even greater decentralization of internet control.
This chapter explores these strategies and tactics developed by TPB admins to elude flow control. My use of “elude” is deliberate. The word comes from Martin Joughin’s English translation of a conversation between Antonio Negri and Gilles Deleuze from the French journal Future Antérieur, which appears in the book Negotiations.[8] Joughin translates the original French phrase “pour échapper au contrôle” as “so we can elude control.” He substitutes “elude” for the French verb échapper, which can also translate as “escape,” “dodge,” or “run away.”[9] TPB’s case resonates with multiple of these meanings of échapper: its use of BitTorrent enacts elusion as a kind of running away, whereas darknets are an attempt to dodge. TPB’s case, then, illustrates the elusion of flow control, building on the limits of control discussed in chapter 1.
Piratbyrån, Accelerationism, and Escalationism
The Piratbyrån, or “Piracy Bureau,” started TPB. The bureau was, by its own admission, “a cluster with fuzzy borders.”[10] From 2003 to its end in 2010, Piratbyrån was a think tank, an alternative news site, an artists’ movement, and a hacktivist project. Schwarz explains: “Part of the hazy nature of Piratbyrån was that they avoided making formal decisions, instead organizing in real time on IRC [Internet Relay Chat].”[11] The name of the cluster parodied the Swedish Anti-Piracy Bureau, a government initiative to thwart copyright infringement. As the Anti-Piracy Bureau tried to find ways to eliminate piracy, the Piratbyrån sought to proliferate it and to embrace piracy not simply as anticopyright, but as a different kind of politics altogether.
This propiracy movement, I have argued elsewhere, has a centrifugal politics.[12] Pirates desire networks without centers, a kind of rhizomatic communication always in flux. This strategy can be witnessed in many of the group’s tactics and in the P2P networks described in chapter 4. Take Kopimism, a concept popularized by the Piratbyrån and now a religion that celebrates the copy.[13] Unlike Creative Commons (its clear inspiration), a Kopimi logo indicates that its creators want people to copy it. In their manifesto, “POwr, xxxx, Broccoli and KOPIMI,” the Piratbyrån offered 100 slogans. Though the absurd, controversial, and political tone of the manifesto resists any one reading, it clearly embraces Kopimism, encouraging its readers to “/join #kopimi,” to “upload,” to “invent or misuse Kopimi,” and to “share files with anyone who wants.”[14] Like a rhizome, Kopimism wants every licensed object to be generative. “To be rhizomorphous,” according to Gilles Deleuze and Félix Guattari, “is to produce stems and filaments that seem to be roots, or better yet connect with them by penetrating the trunk, but put them to strange new uses.”[15] Kopimism captures this rhizomatics that seeks to create not only networks without centers, but networks that undermine central authorities.
This centrifugal approach fits within the long history of piracy. In its many forms, piracy has been a form of communication and, earlier still, of transportation that resists central authority and has undermined the authorized movement of goods, whether under the dominion of queen or capital. In his history of piracy from the high seas to the hackers and phreakers of the late twentieth century, Adrian Johns concludes that piracy is deeply embedded in modernity and in the history of property regimes, so specific manifestations of piracy resist historically specific property regimes.[16] And Piratbyrån’s interest in centrifuge, while not discussed in Johns’s book, contests the mechanism of security and authority necessary for the intellectual property regime.
This centrifugal politics has manifested in confrontations with culture industries, with governments, and with internet daemons. Where the first two confrontations occur in courtrooms and ballot boxes, Piratbyrån’s opposition to daemons occurs in the infrastructure of the internet. To contest daemons, TPB became something like a war machine, a vehicle propelled to stay out of the reach of control. Deleuze and Guattari introduce the “war machine” to describe something outside the state: “It is not enough to affirm the war machine is external to the apparatus. It is necessary to reach the point of conceiving the war machine as itself a pure form of exteriority, whereas the State apparatus constitutes the form of interiority we habitually take as a model.”[17] Like a war machine, TPB had to invent new tactics to elude being captured and itself integrated into the circuits of optimization online.
Rasmus Fleischer, one of the key members of the group and now a prominent academic, reflected on these tactics in a 2010 blog post. His reflections are worth quoting at length:
In 2005, we arranged with Piratbyrån a May Day celebration. It was, if I remember it right, just at the time when Sweden was about to implement harsher copyright laws, and even politicians began to realize that the regulation of file-sharing activity was actually becoming political. The celebration, however, was not in a mood of sadness or protest, but rather a joyful affirmation of the openness of P2P networks. One of the slogans: “Welfare begins at 100 mbit.” Accelerating digital communications and enabling access was fresh strategies which produced a kind of politics which did not fit into the Swedish party system. This accelerationism also enabled a certain political transversality and new alliances between hackers, artists and intellectuals, and it could quite easily be underpinned by a mainstream deleuzianism and/or benjaminism. All this while entertainment industries kept clinging on to the model of selling “units” (cd, dvd).[18]
The freshness of piracy certainly inspired political tactics, such as the rise of the Swedish and later European pirate parties (though they are largely unaffiliated with the Piratbyrån), but it also inspired the cultivation of new tactics to thwart attempts to control the internet. He characterized these tactics as “accelerationism.” The term reflects some of the unpredicted success the group had just experienced. Two years earlier, the Piratbyrån had launched TPB. The public website became a phenomenon, as will be discussed later, actualizing a popular embrace of copying and sharing. The success, however, did not last.
In the same blog post, Fleischer noted an emerging turn away from these tactics: “We certainly do not call for accelerated communications any more.” Political interest had shifted, and the movement had begun to turn back from its prior strategy: Fleischer now suggested a switch from growth to hiding. He called, tentatively, for an “escalationism” characterized by adopting tactics such as encryption, darknets, and tunneling. His comment resonated with a turn to tunneling by TPB with the launch of its iPredator VPN discussed later on.
Accelerationism and escalationism are two strategies developed by the Piratbyrån that eluded control. Accelerationism eluded control by moving faster than or outrunning the modulations of daemons, tactics that stay ahead of a daemon’s gaze or grow faster than can be contained. Escalationism, conversely, dodged control; it is fatalistic, in contrast to the optimism of accelerationism. Escalationism tried to be hidden, though not unknown, to control—at least for a time. Both these tactics raise important questions for the study of flow control.
Fleischer’s use of accelerationism predates the recent academic interest in accelerationism, particularly the attempt to create a progressive accelerationism in light of its dark interpretation by Nick Land.[19] Land’s accelerationism interpreted a passage by Deleuze and Guattari that a revolutionary path might not “withdraw from the process, but to go further, to ‘accelerate the process.’”[20] Land, who has been called a Deleuzian Thatcherite by a foremost theorist on accelerationism, Benjamin Noys,[21] interpreted the quote as a call to turn toward capitalism, to accelerate its tendencies, in order to bring about its end. This suicidal turn, depoliticized by antihumanist themes in Land’s thought and subsequent speculative realist work, has been further marred by Land’s participation in the “neoreactionary,” “Dark Enlightenment” movement, which embraces the market so fully it jettisons democracy, diversity, and equality.[22] The concept, however, has moved past these bleak origins. Nick Srnicek and Alex Williams have called for a “left-wing” accelerationism that frees the concept from capitalism and looks to technology and automation as engines of human progress.[23]
Accelerationism has a polysemy: it is capable of being both a call for fully automated luxury communism and a faith that capitalism is a machine sent from the future to destroy humanity. The piratical position to these various meanings is not entirely clear. The embrace of welfare, postscarcity, and high technology advocated by pirates resonates with a positive accelerationism. Yet, there is a degree of fatalism in Fleischer’s later discussion of escalationism as a way to avoid a darker future by triggering a confrontation now. Similar to Deleuze and Guattari’s discussion of acceleration and capitalism, escalationism entertains the possibility of disaster. My ensuing discussion of the Piratbyrån has an unsettled relationship with accelerationism, which requires more critical reflection, especially in reference to critiques of the idea.[24] Such a project is well beyond a discussion of infrastructural politics on the internet, but the ambiguous position of accelerationism in this chapter should serve as a reminder to treat these concepts with caution even as they clarify TPB’s strategies.[25]
Copy and Paste: Accelerationism and The Pirate Bay
A difference in tactics between TPB’s admins and the hacker collective Anonymous illustrates the accelerationist approach. In 2012, TPB’s website faced being banned within the United Kingdom. The British courts ordered local ISPs to block the website.[26] In line with other instances of internet censorship, the block altered TPB’s local domain name systems to prevent customers from locating their servers. Pirates, hackers, and free-speech advocates quickly responded by launching new websites with lists of proxy servers and alternative domain names that allowed Britons to circumvent the block. UKAnonymous2012, a part of the hacktivist group Anonymous, responded in typical fashion by launching a Distributed Denial of Service (DDoS) attack called #OpTPB. The operation targeted Virgin Media, one of the ISPs participating in the block. DDoS is a core tactic for Anonymous and others engaged in politically motivated hacking or hacktivism.[27] TPB admins responded to the DDoS attacks in a Facebook post:
Seems like some random Anonymous groups have run a DDoS campaign against Virgin media and some other sites. We’d like to be clear about our view on this: We do NOT encourage these actions. We believe in the open and free internets, where anyone can express their views. Even if we strongly disagree with them and even if they hate us. So don’t fight them using their ugly methods. DDoS and blocks are both forms of censorship.[28]
Instead of DDoS attacks, TPB’s Facebook post suggested that “if you want to help: start a tracker, arrange a manifestation, join or start a pirate party, teach your friends the art of bittorrent, set up a proxy, write your political representatives, develop a new p2p protocol.”[29] Where UKAnonymous2012 created a spectacle through its DDoS campaign, TPB admins encouraged their users to copy and paste. In the face of threats, TPB’s posts called for more copying; the accelerationist solution was to grow, expand, and intensify P2P networking.
The Pirate Bay website can be considered an accelerationist tactic carried out by the Piratbyrån, who started TPB on November 21, 2003.[30] Rasmus Fleischer recalled: “It started off as just a little part of the site. Our forum was more important. Even the links were more important than the [torrent] tracker.”[31] The tracker site became so popular, however, that the Piratbyrån decided to split it into a separate organization in October 2004.[32] Piratbyrån handed administration to three men in their twenties: Warg (aka: Anakata), Neij (aka: TiAMO), and Sunde (aka: brokep). Their participation was political. Warg stated: “I see the Pirate Bay as a sort of organized civil disobedience to force the change of current copyright laws and the copyright climate.”[33] The three administrators worked in their spare time to run the site and serve as its public representatives. In addition, Mikael Viborg, a prominent lawyer in Sweden, provided legal assistance to the site.[34] And Carl Lundström, a controversial Swedish businessman, helped to fund the site’s launch.[35] This strange mix is further proof of Fleischer’s claim that accelerationism did not conform to conventional Swedish politics.
TPB accelerated the growth of piracy simply by staying online. The website has been among the top five BitTorrent sites on the internet, and as of this writing, it remains online, unlike most sites of its contemporaries.[36] TPB rose to prominence by enduring a series of contractions of mass piracy beginning with the demise of Napster in 2001.[37] P2P file sharing suffered setbacks due to legal actions and attempts to commercialize on the part of some of the platforms themselves. Court cases shuttered the leading P2P applications, beginning with KaZaa, Morpheus, and Grokster in 2005, and then Limewire in 2010.[38] Numerous search engines that were started to help users find BitTorrent swarms disappeared due to legal pressure and court rulings.[39] While many of these applications succumbed to legal actions, it is important to note that commercial and community pressures also led to contractions in the size of mass piracy. KaZaa, for example, bundled its ostensibly free software with obtrusive spyware and adware. Limewire, on the other hand, sold a “professional” version of its software that promised faster downloads and searches. All these networks disappeared, but TPB survived and kept attracting users.
Given the popularity of other file-sharing protocols in 2003, the Piratbyrån’s decision to use the BitTorrent protocol appears to be a tactical choice. At the time, the protocol was relatively unknown, having been released only in 2001.[40] Bram Cohen, the developer of BitTorrent, announced the new network on a mailing list dedicated to decentralization and the implications of the End-to-End principle (E2E). To be clear, there is no formal link between the idea of accelerationism and BitTorrent. Rather, the protocol has tendencies emphasized by the Piratbyrån. Some technical explanation clarifies this point. BitTorrent networks break files down into pieces. BitTorrent daemons frantically exchange pieces of the file, making sure that every peer has a copy. Pieces do not have to be sent sequentially. Instead, a daemon collects one piece from one peer, another from a different peer, and so on. Through constant exchange of these pieces, a network ensures each user receives a complete copy of the data being shared.[41] There is no client or server; rather, daemons simultaneously upload and download data. Continual exchange between peers means that multiple copies of a piece exist in the swarm, ensuring the decentralization of the file into the network.
The BitTorrent protocol encourages symmetrical uploading and downloading (as Comcast discovered, described in chapter 4). The more one shares, the more one receives. Users who do not share are choked: daemons will stop sending data to them. In this way, BitTorrent programs collectively organize their networks to ensure all nodes contribute data to the network. This strategy is reflected in how the network treats new users. New users do not have anything to share, so they start already choked. As such, new users are three times more likely to benefit from a feature known as “optimistic unchoking,” in which a node decides to send pieces to a user even if that user has been classified as choked. Typically, programs will attempt to share the rarest piece of a torrent. Once a node has pieces and starts sharing them, other nodes recognize that it is sharing and unchoke the connection to send it more files.
Canadian ISPs provide a good description of BitTorrent’s consequences to infrastructure, but their comments need some context. In 2009, the Canadian Radio-Television and Telecommunications Commission (CRTC), a key regulatory institution of the Canadian internet, held hearings on the use of DPI and traffic management techniques. The hearings summoned manufacturers, ISPs, and public-interest groups to debate a framework eventually referred to as Canada’s Network Neutrality Rules. (The ruling, discussed later, remains contentious.) Bell Canada, one of Canada’s biggest ISPs, claimed in their filings to the hearing that P2P file sharing was a corrosive technology that uses a disproportionate amount of bandwidth compared to other types of traffic.[42] Their assertion that file sharing is disproportionate reflects BitTorrent’s accelerationism, as it grows by constantly creating more and more connections between peers. This growth conflicted with Bell’s expectations that one computer establish a limited number of connections to other hosts, from a node to a major server. In contrast, BitTorrent creates a swarm of connections between many users. BitTorrent traffic expands between peers, establishing hundreds of connections to share different bits of the same file. The increase in connections between peers strains the capacity of infrastructural resources.
As much as BitTorrent (at least in 2009) congested infrastructure, the internet traffic management practices hearings revealed just how much BitTorrent disrupted ISPs’ optimization. Another large Canadian ISP, Rogers Communications, argued: “[P2P file sharing is] the least effective method of transmitting data. The cost of bandwidth on the last mile access network to the home is much greater than the cost of bandwidth in a traditional file server.”[43] In other words, P2P is suboptimal, and its traffic shaping reflected that opinion. Rogers disclosed their use of DPI to limit all P2P file-sharing uploading to a maximum of eighty kbps.[44] Bell stated that they throttled BitTorrent, Gnutella, Limewire, Kazaa, eDonkey, eMule, and WinMX traffic on residential networks. Throttling limited download speed to 512 kbps from 4:30 p.m. to 6:00 p.m. daily and reduced it further to 256 kbps after 6:00 p.m. The caps rose at 1:00 a.m. back to 512 kbps before being turned off after 2:00 a.m.[45] Since their optimal internet clearly favored hubs, it should come as no surprise that both Rogers and Bell started numerous video-on-demand services that relied on the traditional client–server relationship with central servers delivering multimedia content. While there is no explicit link between degrading P2P and promoting comparable video-on-demand services, the ISPs’ attitude reveals a trajectory for network development in which the owners have more control over the priorities of the network. To be fair, their activities are not sinister, but they do constitute a network optimization in conflict with the Piratbyrån’s centrifugal desires.
While the BitTorrent protocol decentralizes P2P networking, it does require some central index of torrent swarms and, in the past, a tracker to coordinate sharing. A number of websites arrived to fill this void, including TPB, but in doing so, became easy targets for copyright enforcement agencies. To be more difficult to take offline, TPB adopted developments in the BitTorrent protocol that reduced potential chokepoints, as well as legal accountability. First, TPB stopped coordinating the activities of its peers (technically it stopped running a tracker) in November 2009.[46] Instead, users took on the role of coordination through a technical innovation known as Distributed Hash Tables (DHTs). Second, its admins announced in January 2012 that they would cease hosting any torrent files in favor of Magnet links.[47] The Magnet uniform resource identifier scheme gives directions on how an application might find content on the internet without specifying a location. Client applications search DHTs and peer exchanges using the Magnet link metadata to locate and then start sharing a file.[48] As a result of this change, TPB shrunk down to ninety megabytes and could, therefore, be easily backed up and transported.[49] At the time, TPB admins joked about putting its small index on autonomous drones and sending them out through the city as a distributed network. Finally, the group announced that it had stopped running on its own servers in favor of hosting the entire service on shared servers distributed across the globe (similar to the approach used by WikiLeaks until it was shut down by Amazon). Although TPB admins had toyed with moving their servers offshore or into secure bunkers,[50] they still relied on a centralized cluster of servers hosted in Sweden until October 17, 2012, when they moved to cloud servers.
With the rise of advanced traffic management came a need to rethink the tactic of accelerationism. As early as 2006, one of its members, Neij, suggested “the Pirate Bay will outlive its usefulness.”[51] Accelerationism now seems of a time when the internet might grow to become a digital commons faster than it could be shut down. TPB fit within a general optimism about free knowledge, sharing, and excess. For pirates, this optimism period ended, along with accelerationism as a strategy.
Pirates turned to escalationism. Fleischer, reflecting on the end of a politics of acceleration wrote, “in 2010, we are tunneling communications.”[52] By “tunneling communication,” he meant both an analogy to tunneling underground to avoid detection and a technical term that refers to routing communications through encrypted or obscure channels. Constructing darknets—private, obscure networks on the internet—exemplified the escalationism tactic.
Escalationism might also be understood as an interpretation of Deleuze’s own speculations on new weapons in a control society. In an interview with Negri, Deleuze suggests that:
Maybe speech and communication have been corrupted. They’re thoroughly permeated by money—and not by accident but by their very nature. We’ve got to hijack speech. Creating has always been something different from communicating. The key thing may be to create vacuoles of noncommunication, circuit breakers, so we can elude control.[53]
The idea of noncommunication might not mean simply to stop communicating, but to question the very expression of communication. Elsewhere, Deleuze defines communication as the transmission of information or order-words.[54] To stop communicating would not be to stop talking, but to stop the widespread distribution of an information system or, to borrow from Deleuze, a “system of control.” Given the ubiquity of flow control, fleeing no longer seems viable. Accelerating assumes a free horizon, whereas Deleuze suggests the creation of a “vacuole,” a term from the Latin vacuus, meaning an empty or open space. This method requires tactical meaninglessness, or at least meaningless to daemons. The next section explores the tactic of escalation as a way to obfuscate traffic from the daemon’s gaze.
Hide and Seek: Escalationism and IPREDator
TPB’s admins’ foray into escalationism happened in response to changes in Swedish law. On April 1, 2009, the Swedish government ratified Directive 2004/48/EC of the European Parliament and of the Council of April 29, 2004, on the Enforcement of Intellectual Property Rights (also known as the Intellectual Property Rights Enforcement Directive, or IPRED). The introduction of IPRED closed the loopholes that allowed TPB to operate legally in Sweden. The directive further allowed for greater police monitoring of the internet, in part through the packet inspection daemons of national ISPs.[55] IPRED’s introduction led to a change in tactics associated with TPB.
TPB launched a VPN service mockingly named IPREDator. They announced the service on the homepage, an important and oft-used tactic by TPB. Like Google’s “doodles,” TPB changes the logo on their front page to publicize events, campaigns, and issues.[56] In this case, TPB’s admins posted a screenshot from the Nintendo video game Mike Tyson’s Punch-Out that depicted the game’s protagonist, Little Mac, fighting Glass Joe, an early opponent who is easily defeated due to his characteristic glass jaw. Below the image, a headline announced “IPREDator IS ONLINE” and “Sign up Now for Multiplying Combo.”
Their IPREDator service is an example of what Finn Brunton and Helen Nissenbaum call “cooperative obfuscation,” a tactic that seeks to collectively obfuscate data collection. The Onion Router (TOR) exemplifies this practice. TOR is a distributed network formed by home computers volunteering to route the data of their peers anonymously. The relays anonymize and encrypt data and disrupt the tempo of packet transmission to prevent the kind of flow inspection discussed earlier. The collective efforts of nodes thereby enable a darknet. Another example is the Invisible Internet Project (I2P), which also promises traffic anonymity and security through a similar distributed network. These tactics are also called “circumvention” technologies. Anonymous and Telecomix, both prominent hacktivist groups, have developed secure tunnels and network connections for dissidents in nation-states with censorious regimes, most recently in Egypt and Syria.[57] Their efforts continue a long history of developing anticensorship proxy services like the Citizen Lab spin-off Psiphon and proxy servers.
IPREDator was a privacy-oriented VPN service. Today, such services are popular, but at the time, a consumer markets for VPNs was nascent. IPREDator, in other words, helped popularize VPNs as a privacy enhancing technology. Sunde explained that IPREDator sought “to hide from what the government does in the form of giving companies police powers.”[58] He meant that governments had mandated ISPs to watch for copyright infringement and security threats. Well before the recent popularization of VPNs to avoid geo-blocking (e.g., blocking Canadians from accessing Netflix’s larger American catalogue) and the rise of other similar services, IPREDator provided a VPN that tunneled subscriber communications through trusted servers in Sweden. The tunnel is a secure and encrypted link between the home user and the IPREDator’s servers. This arrangement protects subscribers’ traffic from being monitored by their local ISP, and it allows subscribers to anonymously connect to the internet. The IPREDator servers anonymize traffic. Outside servers know only that they have a connection from the IPREDator servers, rather than from specific customers. The service initially cost a flat five euros per month and did not charge by usage.
IPREDator appropriated VPNs from their traditional business uses. VPN technology started as a way for businesses to maintain a private network on the common internet. Researchers at AT&T in the United States and the United Kingdom proposed VPNs in 1988 as a way to use public networks privately. This meant creating autonomous and encrypted networks running on public infrastructures.[59] A number of VPN protocols developed, including Point-to-Point Tunneling Protocol (PPTP), Internet Protocol Security (IPSec), Point-to-Point Protocol over Ethernet (PPPoE), OpenVPN, and Layer 2 Tunneling Protocol (L2TP).[60] While IPREDator currently uses the GNU Public License OpenVPN, it started with PPTP, which establishes a direct link between a client server and a VPN server. All traffic from the client (a request to a website, for example) flows from the client to the VPN server, out to the internet, and back to the VPN server, where it returns the information to the client. PPTP emerged out of research conducted by a consortium of companies, including Microsoft and 3Com, that led to Request for Comments (RFC) 2637, posted in July 1999.[61] While the protocol does not outline any encryption for its tunneling, IPREDator uses 128-bit encryption using Microsoft Point-to-Point Encryption for traffic and the Microsoft Challenge Handshake Authentication Protocol to log into the VPN.[62] This encryption prevents daemons from looking into the packet to see its contents.
Trygghetsbolaget i Lund AB, a firm that had worked with the Pirate Party in the past to create political VPNs, handled their VPN services. IPREDator operates as a “pre-paid flat-rate service” because this business model, they claimed, has the lowest reporting requirements, since they do not have to log and charge for usage. IPREDator does not keep logs of users, since IPRED does not mandate data retention.[63] IPREDator’s security page claims that they would cooperate with Swedish authorities only in the event that a user may be facing jail time and that, furthermore, for “inquires from other parties than Swedish authorities IPREDator will never hand over any kind of information.”[64] Given that their service attracts international customers, they again appear to be playing international laws to their advantage, forcing international legal cooperation before releasing any data to an international user’s local authorities.
The Packeteer PacketShaper 8500
How IPREDator obfuscates traffic warrants some more technical explanation. To do so, I use a lab environment to simulate detection and obfuscation tactics (a common practice in computer science). To perform the simulation, I gained access to a used Packeteer PacketShaper 8500 connected to the internet. Access to traffic management equipment like the PacketShapter 8500 is difficult, and so the following section offers a rare window into the management of these middleboxes. In the lab, I connected a stock Windows computer to the PacketShaper, which was, in turn, connected to the internet, not unlike a home user passing through an ISP’s infrastructure to connect to the general internet. The Windows computer had to connect to the internet through the PacketShaper. I had direct access to both devices, allowing for both the simulation of traffic on the lab computer and direct configuration of a foundational DPI appliance.
Packeteer led the field in advanced traffic management from its founding in 1996 until its acquisition by BlueCoat in 2008.[65] The most robust appliance in their product line circa 2002, the PacketShaper 8500 handles 200 megabits per second to delineate a maximum of 500,000 IP flows into over 5000 classes, partitions, or policies. Since many networks routinely use more than 200 mbps, the software clearly has its limits. More recent DPI devices are able to handle much higher loads of traffic.
A pamphlet for the product suggests that it is “the answer to service providers’ demands for a high-capacity solution that delivers differentiated services, ensures fair and equal access, enforces user policies and improves profit margins through various co-location services.”[66] A review of the newly launched project stated that “the largest demographic for peer-to-peer file sharing is college students” and that the PacketShaper is a serious asset “in a university environment, where protocols such as those associated with Kazaa and Gnutella are clogging up the pipes”; however, P2P protocols “disguise themselves via HTTP tunneling or using multiple ports” (a phenomenon previously discussed in chapter 4 as “port spoofing”). To compensate, the review continued: “[The PacketShaper] looks at more than just port number. Instead, it examines application signatures.”[67] Comcast faced an identical problem, as P2P networks also used port spoofing to avoid detection.
The PacketShaper 8500 is administered through a web interface. The interface includes ways to classify and manage networks, like other DPI appliances discussed earlier. Its class-based perspective consists of a tree of traffic classes grouped into inbound and outbound.[68] The order of the tree determines the match. Like a hand moving down a list, the PacketShaper runs through the tree from top to bottom, matching information in a packet to patterns in classes. For HTTP (HyperText Transfer Protocol), FTP (File Transfer Protocol), and NNTP (Network News Transfer Protocol) networks in particular, the Packeteer 8500 allows for even more granular classification. Like other DPI boxes, the PacketShaper could target Firefox clients browsing TPB while allowing all other HTTP traffic to flow normally. It could match FTP packets based on file names or extensions. Also, the PacketShaper could identify the binary groups that were havens for pirated content on newsgroups (NNTP).
The tree changes when Packeteer releases an update, when administrators add classes, or when the PacketShaper discovers new patterns on its own. Most vendors release updates that add new classes based on their own monitoring of traffic pattern trends (as exemplified by Arbor Network’s ATLAS program, discussed in chapter 4). Each traffic class includes a list of rules for the PacketShaper to follow to identify a packet. Does its header contain a declaration of being part of a BitTorrent network? Do the packet contents include commands associated with FTP? In addition to these prepackaged classes, the PacketShaper also automatically adds classes when set to “traffic discovery” mode. The automated mode searches for repeating traffic patterns and creates new classes once it recognizes the same pattern three times. A network administrator might leave the appliance in discovery mode for a week or so to generate a list of popular applications before turning it on and letting it run.
The PacketShaper manages classes through policies and partitions. Policies, according to the manual, manage individual flows, while partitions manage aggregated flows (similar to classes and policy maps in Cisco’s Internetwork Operating System, or IOS). A difference, in other words, of granularity, where a policy allows a network to “to manage bandwidth on a flow-by-flow basis” and a partition groups packets “so that all of the flows for the class are controlled together as one.”[69] A policy could apply to HTTP, where HTTP could also be part of a partition that includes FTP and email. The manual suggests creating rules that protect “mission-critical” traffic while shaping “aggressive traffic.” Policies and partitions set the modulations of daemons to guarantee a bit rate, set the priority in the queue, pass the traffic through the network, impose DiffServ or MPLS (Multi-Protocol Label Switching), or block traffic altogether. Policies can simultaneously block malicious content, ignore normal activities so packets travel according to best efforts, and guarantee bitrates for value-added traffic. The most common function would be to guarantee a minimum and maximum bitrate to ensure proper application functionality. Along with guarantees, a policy might also allow a flow to burst—that is, to temporarily send more bits than it rates—according to a priority and a limit. A partition, like a slice of pie, divides the available bandwidth into sections that have a fixed capacity.
IPREDator eludes the PacketShaper by avoiding its gaze. As part of the experiment, seen in Figure 10, I monitored the real-time graph included in the PacketShaper’s web interface to interpret the daemon’s gaze. The graph plots the network’s bandwidth consumption over time. To test this gaze, I attempted to duplicate the experience of an IPREDator user seeking to avoid traffic management targeted at BitTorrent. I downloaded a torrent of the Ubuntu Linux distribution using version 5.2.2 of the BitTorrent client from roughly 2009. While the lab computer opened and connected to the Ubuntu torrent’s network, the PacketShaper monitored BitTorrent (labeled Outbound/BitTorrent and Inbound/BitTorrent) and VPN traffic (labelled Outbound/GRE and Inbound/GRE). As the download began, Inbound/BitTorrent traffic spiked upward. Since the PacketShaper easily recognizes BitTorrent traffic, it can just as easily throttle it. Under the “manage” tab, one can select policies or partitions to limit the flow of BitTorrent traffic. For this experiment, I set a partition of fifty kilobytes per second. After one minute, shaping kicked in. The Inbound/BitTorrent line dropped until it plateaued at the set limit. On the lab computer, the download slowed down too. If the application of the PacketShaper to the BitTorrent traffic exemplifies the daemon’s reach, then IPREDator attempts to loosen its grip. Logging on to IPREDator completely alters the flow of packets. Repeating the test from above, when a shaped BitTorrent exchange logs into IPREDator, its traffic drops as it changes addresses on the internet; however, as its location stabilizes and the client reestablishes contact, the traffic stabilizes and climbs past the set limit of fifty kilobytes per second to communicate at the same rate as before.
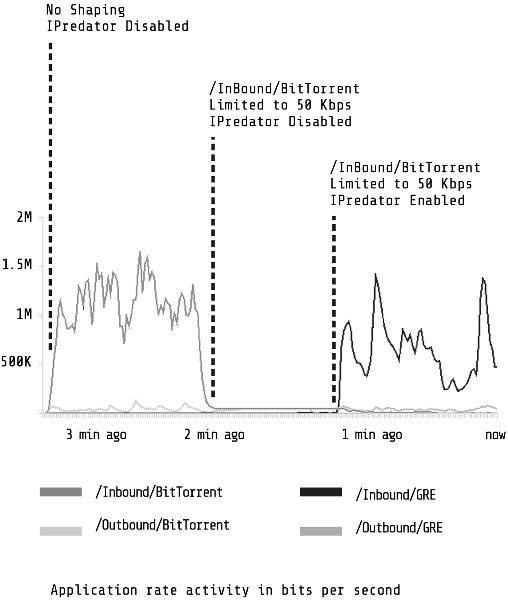
Figure 10. BitTorrent performance with and without iPredator virtual private network enabled.
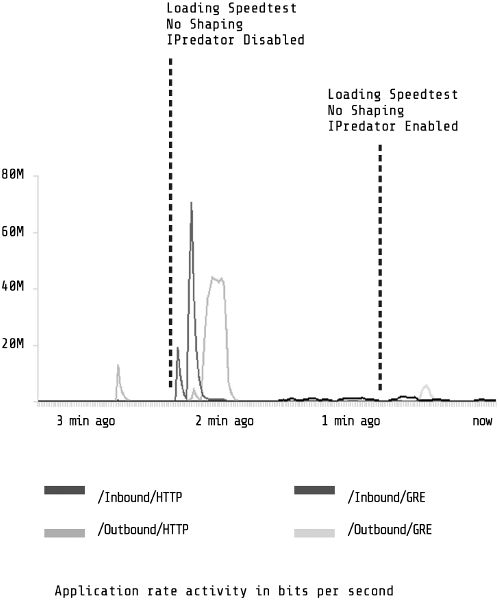
Figure 11. SpeedTest performance with and without IPREDator virtual private network enabled.
The results distinguish accelerationist and escalationist tactics. IPREDator, in contrast to TPB, is slow; it actually degrades performance. Figure 11 depicts the results of another experiment using a popular internet performance test called SpeedTest. I performed the test with and without IPREDator enabled and monitored the results using the same PacketShaper interface. Without IPREDator, download speeds reached 80,000 kbps and upload speeds reached 40,000 kbps. Though hard to see at the far right of the graph, tests using IPREDator reached a mere 5,000 kbps download, and upload speed was even slower. Importantly, the delay was not a result of the Swedish traffic having to connect to the United States, a longer distance to travel. SpeedTest has testing servers located in Sweden, so when I ran the IPREDator-enabled test, it connected to a Swedish testing server. The advantages of IPREDator are obscurity and autonomy, not speed.
IPREDator illustrates the second tactic of TPB related to escalationism. IPREDator privately transmits BitTorrent packets, but publicly they appear as VPN traffic (specifically Inbound/GRE and Outbound/GRE, according to the PacketShaper). The service hides contraband traffic among the more desirable corporate traffic of the internet. IPREDator is a tool of escalationism not because it hides the traffic perfectly, but because it obfuscates it. This camouflage makes it more difficult for daemons and blurs their gaze. While the PacketShaper can simply add a new filter to manage GRE traffic, it does so at the risk of also affecting commercial VPN traffic. Most VPN traffic comes from corporations who use it to secure communication between an employee in the field and company servers. In a sense, IPREDator hides BitTorrent networks among corporate ones, taking advantage of the fact that ISPs cannot manage VPN traffic too greatly without the risk of alienating business customers.
Escalationism is now a larger tactic employed by pirates, hacktivists, and P2P developers to struggle against, but not escape, control. Escalationism hides from advertising, social media profile tracking, and state surveillance. Tactics include various forms of obfuscation that produce “misleading, false or ambiguous data to make data gathering less reliable and therefore less valuable,” as Brunton and Nissenbaum describe them, including time-based obfuscations that temporally disrupt surveillance, selective obfuscations that jam data mining by specific sites like Facebook, and ambiguating obfuscations that “render an individual’s data permanently dubious and untrustworthy as a subject of analysis.”[70] The BitTorrent extension Hydra, for example, injects dummy requests and other misinformation to confuse analysis of its traffic, and so the user’s activities are never apparent to those watching. Darknets created by TOR or I2P encrypt traffic and route messages between peers to be less attributable to the source. New private channels like Slack and Discord create communities hidden from search engines but easy to find. VPNs like IPREDator are just one of many forms of escalationism today.
The Most Disastrous Escalations? Reckoning with the Pirate Bay
Accelerationism and escalationism were both strategies invented by TPB, but they function as more general concepts to understand resistance to daemonic optimization. These strategies function like a war machine. Deleuze and Guattari write that “the war machine invents speed and secrecy.”[71] The Piratbyrån chanced upon BitTorrent as a radical speed, an accelerationist speed. The website became something independent from them, not necessarily under their command. It grew rapidly and globally. Escalationism, in turn, deals in secrecy. Both strategies endure online, with hackers looking for new proliferate kinds of rapid networking or better ways to go dark. Speed and secrecy might be seen as the new weapons about which Deleuze speculates in his discussion of elusion and control. While these tactics might elude daemons, I wonder about the effectiveness of the overall strategy of invention.
Daemons are never idle. Deleuze and Guattari, in the same quote above, suggest that “there is a certain speed and a certain secrecy that pertains to the State, relatively, secondarily.”[72] That is to say, the war machine is not defined by the state, but it does inspire a response from the state apparatus. The worry is that these strategies function as a reason to improve flow control precisely because they attempt to elude it. Control grows through its opposition. Deleuze and Guattari describe the same dynamic for the war machine, that it propels the state by defining its limits, by being what it cannot capture:
[The war machine] is a kind of rhizome, with its gaps, detours, subterranean passages, stems, openings, traits, holes, etc. On the other side, the sedentary assemblages and State apparatuses effect a capture of the phylum, put the traits of expression into a form or a code, make the holes resonate together, plug the lines of flights, subordinate the technological operation to the work model, impose upon the connections a whole regime of arborescent conjunctions.[73]
Plugging holes and imposing connections are all a kind of productivity. These responses show the risk of these tactics. Far from eluding control, they might make it even worse. Remember that Packeteer sold its PacketShaper as a solution to out-of-control piracy on academic networks in the quotes above. Piracy justified an investment in control.
Even more unsettling is that these moves might have been anticipated by the Piratbyrån. Fleischer explains that the motivation for escalation was not escape. Fleischer’s goal was to escalate the activities of the daemons toward some sort of greater confrontation. By contrast, Brunton and Nissenbaum list six reasons for obfuscation, from buying time to expressing protest. The underlying strategy of escalationism was to provoke, to trigger a confrontation. Fleischer compared tunneling to concerns about wiretapping that “would only escalate encryption and tunneling—which, in its turn, will surely provoke legislators to attack darknets, and so on, as a positive feedback loop out of control.”[74] Darknets, encryption, and protocol obfuscation all provoke daemons. To Fleischer, at the time, that was the point:
However, we could say that escalationism does not have escalation as its object, any more than the war machine has war as its object. It might even have more to do with preventing the most disastrous escalations. One way to do it might be to let the escalation happen before it becomes disastrous. But it is in the nature of escalationism that there is no subject that can judge the right timing, before the whole thing has escalated into something else.[75]
Escalationism hopes to provoke a confrontation sooner rather than later, hoping that the conformation is on better terms. Less abstractly, the goal of going dark now is to provoke questions about daemons now, rather than allow more capable daemons to be developed in the future. Escalationism may be seen as a strategy of secrecy and publicity. Will they be better or more disastrous? Fleischer ends without clarifying what he means by a disastrous escalation, but the intent is clear. Escalationism is a risky path that might provoke something far worse than present flow control. Yet, the ways this strategy hoped to make public and mobilize around the confrontation remained unclear.
The ambiguity of accelerationism and escalationism does not imply that piracy has exhausted itself. Perhaps the propiracy movement could offer more of an intervention in media policy than an elusion of flow control. What would an accelerationist optimization be? The radical sharing of BitTorrent could inspire a new form of traffic management in which performance is common to users. What would happen if infrastructures abandoned service tiers and accelerated networks? In keeping with the accelerationist spirit, that might mean an embrace of artificial intelligence and an intelligent infrastructure. It might involve taking Saisei’s FlowCommand at its word. Mentioned in chapter 4 as an example of a fully autonomous policy daemon, FlowCommand promises to be “the world’s first ‘Net Neutrality’ enforcer.”[76] Could such an intelligent daemon impose fair bandwidth for all users? Maybe an iso-synchronization in which all nodes have equal bandwidth?
Further, what would an escalationist optimization be? An infrastructure that is unknown or unknowable? Could pirates undermine the growing concentration of data? At a time when the internet has become a standing reserve of data on demand for surveillance agencies and corporations alike,[77] could escalationist optimization create networks without concentrations of knowledge, without aggregations of data that tempt marketers, corporations, law enforcement, and surveillance agencies? The outcome might be a much more disconnected internet, like the kinds of mesh wireless infrastructures being installed in cities such as Barcelona, Kansas City, and Montreal. These infrastructures can be local pockets of connectivity with bounded limits on the circulation of information.[78] An escalationist optimization could valorize these borders, creating points beyond which data will never aggregate.
Conclusion
Risky infrastructural tactics were not the only interventions by TPB’s administrators. They also influenced internet culture and cultivated global opposition to increased copyright enforcement. The raid catalyzed the Swedish community around the group and fostered the nascent pirate movement. Swedish youth who grew up with computers and digital networks began to engage politically in response to the raid. The police raid inspired a growth in membership in the Swedish Pirate Party as young Swedes expressed their outrage and pushed the party into the public spotlight. Pirate parties spread throughout Europe and North America.[79] TPB’s administrators, for their part, continued their infrastructural struggles within the legal system. The police proceeded with their case and filed charges on January 31, 2008, two years after the raid. The trial began a year later in February 2009 and ended in April that same year. TPB appealed, and the court case truly ended only when the group lost their final appeal in 2012. The Swedish court found them guilty. The three administrators were sentenced to roughly a year of jail time and fines totalling $6.5 million.[80] Losing the court cases did not shut down the website, as the Swedish Pirate Party began to host the site.[81] Even though the site administration has changed since, TPB (as of this writing) is still online. Current administrators keep a lower profile, although they continue to post on the site’s blog and in its Facebook group (aptly named “The Pirate Bay War Machine”).[82] TPB continues to be one of the top BitTorrent sites in the world.[83]
If, at the end of this chapter, elusion seems a fraught response to daemons, what are other ways to confront them? In the final chapter, I turn from these more theoretical questions to examine policy matters that relate to daemons. Policy makers, as much as pirates, have attempted to respond to the issues raised by flow control. Usually their approach to the matter draws on the concept of net neutrality. Making flow control matter to policy makers offers a new set of challenges that help further elaborate the concept. What does the concept of flow control reveal? How does it reconceptualize the internet in contrast to net neutrality? What normative approaches does it offer that could lead to sound policy? The next chapter delves into the relationship between the public and flow control through a review of an important network neutrality enforcement case in Canada.